Unveiling the Importance of Security Testing in OutSystems Applications
In an era where digital landscapes are battlegrounds, security, and cyber attacks have emerged as pivotal themes. Think of it as modern warfare without gunfire but with equally significant consequences. This unseen battlefront is critical yet shrouded in a veil of mystery with much left to discover and understand.
This article aims to shed light on the crucial role of security testing in applications, emphasizing those developed using OutSystems. We'll explore why it's essential to prioritize these tests in an environment where digital threats are both ever-present and continually evolving.
Understanding Cyber Attacks and the Underlying Motives
A cyber attack is an illicit endeavor by hackers to gain unauthorized entry into a system or network. Their goal? To disrupt, disable, modify, corrupt, seize control, or steal sensitive data. These attacks meticulously target data integrity and often aim to expropriate controlled information.
It all starts stealthily with random attacks across different industries or companies. Hackers or programmed computers scour for weaknesses, exploiting even the smallest system vulnerabilities. Once they identify vulnerabilities, the attacks intensify, burrowing deeper into the network. The end game is usually monetary gain – either through ransom demands from the affected entities or by selling the stolen information.
Sometimes, an attack is detected only a long time after the damage to the infrastructure has been inflicted.
So, what kind of information holds value for cybercriminals? Usually, they steal confidential data, intellectual property, or prototypes of potential products to sell or leverage for ransomware.
OutSystems applications, often central to data management, are likely targets; therefore, particular attention is needed to shield company and customer data.
Internal vs. External Applications: Navigating Security Landscapes
An internal application is confined within a specific domain and is accessible only to users within that domain. While the security risks in such applications are relatively lower, it is essential to remember that this does not make the servers hosting these applications immune to cyber attacks.
Common security breaches in internal applications include unauthorized system or network access, which could occur through hacking or the unauthorized use of account credentials.
Conversely, an external application is accessible to users outside the domain, thus introducing a higher number of vulnerabilities and requiring heightened security measures.
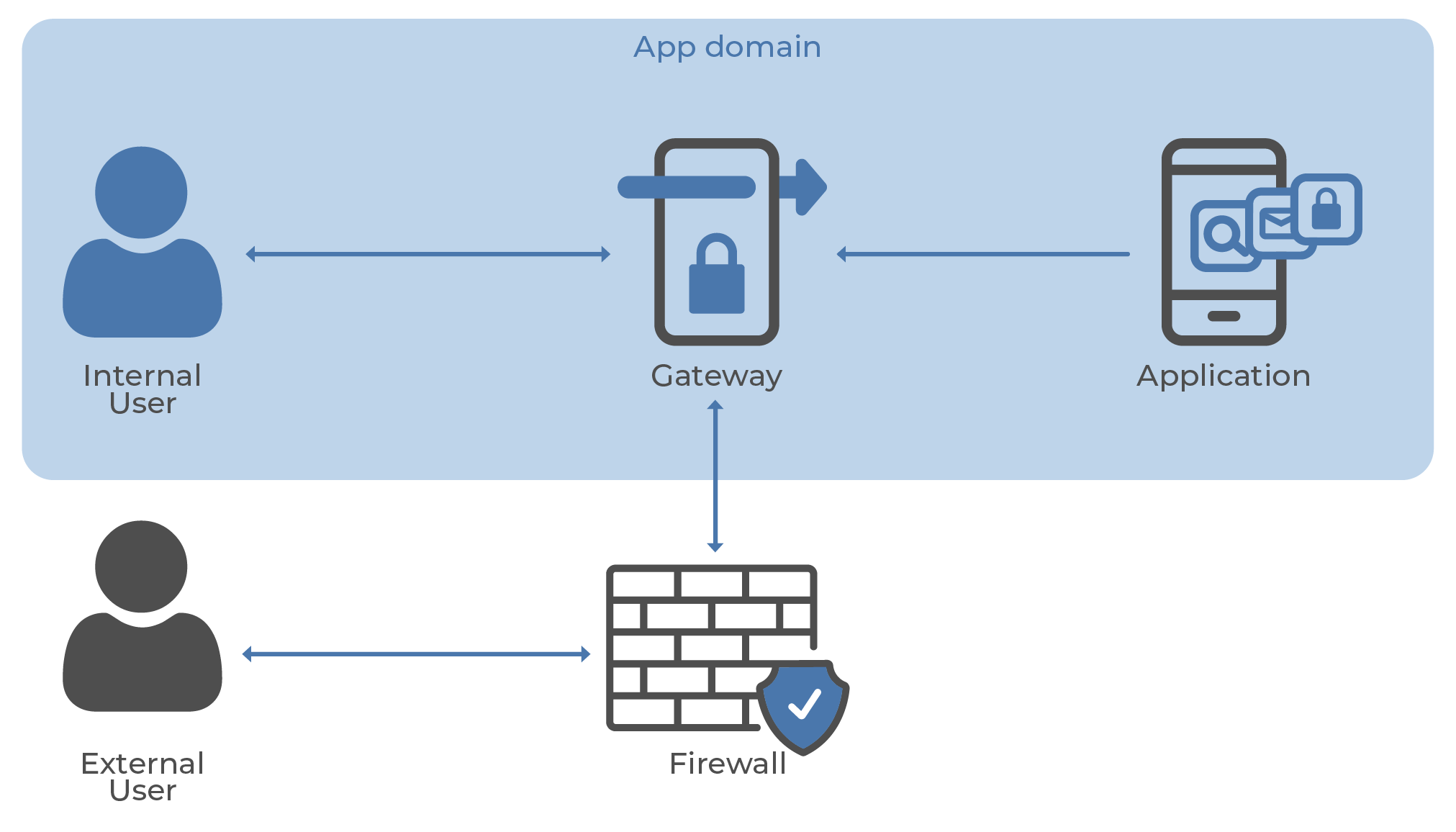
The accompanying image provides a standard schematic of the architecture recommended for different user types. While this architecture does not protect against all risks and vulnerabilities, it delineates the security considerations for internal and external users.
In terms of security measures, firewalls play a crucial role. They identify and filter out the 'DNA' of malware from incoming data packets, thus preventing malicious assembly within systems. On the other hand, Secure Web Gateways (SWGs) operate at the application layer. They are designed to block access to dangerous websites and applications, providing an additional digital domain security layer.
Learn how to classify Users as Internal in the OutSystems Platform: Classify Users as Internal Users.
Image 1 – Standard schematic of the architecture recommended for different user types
Vulnerability Scanning: A Key to Cybersecurity
Vulnerability scanning is a crucial automated process to identify application, network, and security infrastructure weaknesses proactively. This process is often conducted by third-party security service providers or an organization's IT department. Interestingly, vulnerability scans are also sometimes executed by hackers seeking network entry points.
The core of vulnerability scanning lies in identifying and categorizing system vulnerabilities within communication equipment, networks, and computers. Beyond pinpointing security loopholes, this process also evaluates the necessary countermeasures to thwart potential attacks effectively.
Internal Vulnerability Scanning involves conducting scans from within the internal network. These scans, predominantly performed within the internal network environment, offer in-depth insights into security vulnerabilities. The benefits of internal scans are manifold, providing a proactive defense against various known and unknown threats.
On the other hand, External Vulnerability Scanning, or perimeter scanning, is carried out from outside the network. This type of scan is instrumental in detecting vulnerabilities that pose a risk to assets exposed to the external world, namely the internet. By targeting external IP addresses, external scans reveal potential vulnerabilities and enumerate ports that are openly accessible to the internet, offering a comprehensive view of network security.
For an in-depth exploration of top tools in this field, be sure to read the article 15 Best Network Scanning Tools (Network And IP Scanner) Of 2024.
Navigating the Threat Landscape: Most Common Cyber-Attacks
Cyber-attacks come in various forms; thus, awareness of what they entail is vital for effective cybersecurity. Here's an overview of the predominant threats:
Phishing
This attack involves hackers sending fraudulent messages to trick victims into revealing sensitive information or installing malicious software. Typically, these messages impersonate reputable brands or entities, misleading the victim into believing they are genuine.
Malware
This term encompasses various types of malicious software, including viruses, worms, trojan horses, Ransomware, spyware, adware, and more. The primary purpose of malware is to infiltrate, damage, or disrupt computers, servers, or networks. While financial ransom is a common motive, especially with Ransomware, malware can also be used to gain unauthorized access to systems, steal sensitive data, or cause disruption and damage without a financial motive. The broad range of malicious intents and types makes malware a particularly pervasive and dangerous cyber threat.
Brute Force
This attack strategy forces entry into a system, site, or server by attempting thousands of possible passwords, user logins, and encryption keys in hopes of finding the correct one to gain full access.
Man-in-the-Middle
As the name suggests, this attack occurs when a hacker intercepts communication between two servers, computers, or systems, potentially impersonating one of the communicating parties to capture confidential information.
For a deeper understanding of common web application security risks, consider exploring the OWASP Top 10, a definitive list of web applications' most critical security concerns. Additionally, to see how OutSystems addresses these top 10 security risks, visit How OutSystems Helps You Address OWASP Top 10.
Addressing Common Vulnerabilities in OutSystems
Understanding and mitigating common vulnerabilities is crucial in web and application development. Here's how OutSystems effectively addresses these issues:
Broken Access Control
Access control issues occur when attackers can access, modify, delete, or perform unauthorized actions in an application.
The OutSystems platform has this vulnerability protected by implementing role-based access control. Therefore, an administrator defines the roles of specific users and their permissions, so the application is expected to be only reachable by the right people and with the proper responsibilities.
Learn more: Protecting OutSystems apps from access control/permissions vulnerabilities.
Cryptographic Failures
This vulnerability is related to data protection in transit as if it were a tunnel, and the information has to reach both ends without being changed or damaged.
With OutSystems, you can enable the SSL protocol to force the HTTPS channel to be used. It also allows you to use pre-built components to encrypt the data.
Learn more: Protecting OutSystems apps using encryption and SSL/TLS.
Injection
Injection is one of the hackers' favorite vulnerabilities. All web pages that receive inputs and parameters can easily be manipulated with SQL Injection or Cross-Site Scripting, which injects code into an input to execute some JavaScript code or CSS or modify a URL or attribute.
By default, OutSystems escapes content before showing it on the UI, thus preventing injection. Moreover, the platform offers sanitizing functions useful when using, for example, an SQL query to get more complete information from the database.
Learn more: Protecting OutSystems apps from code injection / cross-site scripting attacks.
Insecure Design
This vulnerability stems from the absence of integrated security controls throughout the application's development cycle.
OutSystems security checks proactively warn developers of potential security issues as they publish their applications.
Security Misconfiguration
This issue is a vulnerability when different rules are defined in various places for the same component or when the rules are poorly defined, set to default, or even non-existent. Some scenarios are, for example, using accounts/passwords that are already set by default, the software is outdated, flaws are not fixed, a secure password policy is not implemented, files and directories are unprotected, blocklists and allowlists to block or allow some targets, and many other cases.
OutSystems provides system administrators with clear and concise instructions on how to make the platform installation secure. In addition, it includes a set of capabilities that allow you to define and implement the security controls required by your applications.
Strengthening Application Security: Essential Best Practices
Ensuring robust application security is a critical aspect of web development. Here are essential actions to strengthen your security posture:
Follow the OWASP Top 10
The OWASP Top Ten contains the most critical web application security vulnerabilities identified and agreed upon by security experts worldwide. By being aware of them, how they work, and coding securely, our applications stand a far better chance of not being breached.
Conduct Application Security Audits
Perform regular security audits to assess files, website core, plugins, and servers to identify loopholes and potential vulnerabilities. Security audits include dynamic code analysis as well as penetration and configuration tests.
Implement Robust Authentication Methods
Secure your systems by ensuring only verified users gain access. Implement robust authentication methods that reliably match user credentials with those in an authorized user database or a data authentication server.
Monitor Security in Real-Time and Provide Protection
Adopt real-time security monitoring to track incident occurrence, reporting, and resolution accurately. Thus helping your organization become more proactive with its response methods and deal with recurring problems efficiently.
Encrypt Sensitive Data
Use encryption to maintain confidentiality, concealing the content of the message by translating it into a code. Additionally, employ digital signatures to guarantee integrity and authenticity, verify the sender of a message, and indicate that the content has not been changed.
Keep Servers and Software Updated
Regular updates can prevent security issues and improve compatibility and program features. Software updates are necessary to keep computers, mobile devices, and tablets running smoothly, and they may lower security vulnerabilities.
As we discuss the best practices for application security, we must recognize the specific approaches and tools available for platforms like OutSystems. To seamlessly integrate these best practices into your OutSystems applications, I highly recommend visiting their comprehensive Reactive Web Security Best Practices guide.
In conclusion, while the landscape of cyber threats constantly evolves, staying informed and implementing these best practices in application security is critical to safeguarding your digital assets. For those utilizing OutSystems, leveraging the platform's specific security features and guidelines is essential for robust application protection.
To dive deeper and expand your skills in OutSystems security, here's a list of valuable resources:
By harnessing these resources, you can effectively manage and enhance the security of your OutSystems applications, staying one step ahead in the dynamic world of cybersecurity.
Like this article? Share it: